Computer Physicians loves Boulder! We are glad to be your full time Computer company in Boulder, CO. We have been in business since 1999. Our office is close by Boulder servicing Boulder regularly. Call us for a appointment in Boulder Colorado. Providing Computer Repair, upgrades, sales, installations, troubleshooting, networking, internet help, Virus removal, and training.
All posts
Corona Virus Update
Computer Physicians, LLC will be accepting safe, mask and glove wearing no-contact drop-off/pick-up, and on-site and remote services during the corona virus pandemic. We prefer if you drop off the computer to our workshop in Longmont (if possible) for computer repair, troubleshooting, sales help.
All posts
Microsoft SCAM Solved
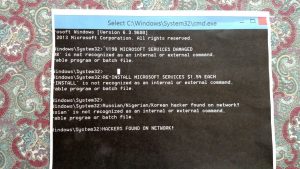
I went to fix a computer from a customer in Erie, Colorado who got scammed from someone that took over their computer on remote access saying they were from Microsoft.
I traced the steps.Very interesting what they did they use the command prompt to put fake commands in saying that hackers were infiltrating your system and they needed to pay money to fix the issue. They said they were from Microsoft and need to fix the problems created by the hackers.
There are no hackers they put fake messages in certain places where you check the system for errors. Here’s a printout of the Windows command prompt with bogus information
People who are not technicians are fooled by this. but this is a command prompt this is not a error screen. That’s why it says it’s an unrecognized command Copying and pasting bogus error information in the command prompt you supposed to only be typing commands People get confused by this who don’t know about computers.
Saying that you must install Microsoft services at $1.54 a piece 198 times for each service. Then they take the credit card information charge your credit card for that and God knows for what else. They also did other things working very fast having the customer do things on the computer to distract your attention and having a lot of pop-up screens. While taking over the computer with remote access.
I was able to undo any damage they caused and get the computer back up and running like before. So in the end I fixed the issue. But people need to call Computer Physicians if they get a problem with their computer so that they don’t cause more issues or problems. This hacker could have done worse if the customer did not call Longmont Computer Physicians to come solve the issue.
All posts
Longmont’s Newest Computer Viruses – Longmont/Boulder CO – Computer Physicians
Computer Repair Longmont, CO Virus removal. – Computer Physicians, LLC
Here is some news about the latest computer viruses out today that Computer Physicians in Longmont/Boulder, CO can help you with:
Technewsworld:
A new ransomware exploit dubbed “Petya” struck major companies and infrastructure sites this July 2017, following last month’s WannaCry ransomware attack, which wreaked havoc on more than 300,000 computers across the globe. Petya is believed to be linked to the same set of hacking tools as WannaCry.
Petya already has taken thousands of computers hostage, impacting companies and installations ranging from Ukraine to the U.S. to India. It has impacted a Ukrainian international airport, and multinational shipping, legal and advertising firms. It has led to the shutdown of radiation monitoring systems at the Chernobyl nuclear facility.
All posts
Longmont Boulder Computer Repair Data Recovery -Video
Longmont Boulder Computer Repair Data Recovery PC service Virus removal.
https://www.computer-physicians.com/ in Longmont, Boulder, Erie, Denver, Colorado. Onsite at your location – we come to you! Onsite, in-shop or remote help. Video about Computer Physicians:
Longmont Boulder Computer Repair PC service Virus removal, Data Recovery https://www.computer-physicians.com/ in Longmont, Boulder, Erie, Denver, Colorado. Onsite at your location – we come to you! Onsite, in-shop or remote help.
All posts
Longmont/Boulder Computer Repair service & sales
Longmont Colorado Computer Repair with Computer Physicians
Computer Physicians provides high quality low cost computer repair, training, help, data recovery on PC Windows and some Mac apple computers in Boulder Denver and Longmont, CO, and worldwide via the internet.
Here is a good article about computer topics questions and answers
COMPUTER REPAIR Questions and
Answers
Original link to the article is here:
1. What is a computer?
2. What are the different functions of a computer?
3. Draw the hierarchical classification of the computer.
4. How a minicomputer different from a mainframe?
5. What is Super computer?
6. Differentiate Input and Output device.
7. What is a storage device? What is the common
classification?
8. What do you mean by a processing device? What are the
various types of processing devices?
9. Differentiates Serial and Parallel port.
10. What is an interface?
11. What is a microprocessor?
12. What are the factors affecting the speed of the
microprocessor?
13. What are the differences between Multitasking and
Multiprocessing?
Multitasking- Enables the processor to do multiple programs
simultaneously by fast switching through the programs. Here
doesn’t have the involvement of multiple processors.
Multiprocessing- Enables the processor to do multiple
programs simultaneously by the use of multiple processors.
14. What the difference between FSB and BSB?
Front Side Bus. Another name for the system bus. The Front
Side Bus connects the CPU to main memory. A microprocessor
bus that connects the CPU to a Level 2 cache is called Back
Side Bus. Typically, a backside bus runs at a faster clock speed
than the Front Side Bus.
15. What is packaging a microprocessor? What are the
different packaging available?
Packaging is the process of connecting a microprocessor with a
computers motherboard. The types of microprocessor
packaging are;
a. PGA
b. SPGA
c. SECC
d. LGA
16. What is LGA ?
An LGA socket is the connection point for a central processing
unit (CPU. to fit into a motherboard. The LGA stands for Land
Grid Array.
17. What is CISC and RISC?
Reduced Instruction Set Computer (RISC. and Complex
Instruction Set Computer (CISC. are two philosophies by
which computer chips are designed. RISC became a popular
technology buzzword in the 1990s, and many processors used
in the enterprise business segment were RISC-based.
18. What is Intel Pentium?
The Intel Pentium is a series of microprocessors first
developed by the Intel Corporation. These types of processors
have been found in many personal computers since 1993.
19. Any difference between Pentium III and IV.
There have been a number of Pentium processor lines starting
with the base Pentium in 1993.The of the recent Pentium
entries are Pentium III and Pentium 4.
a. In a Pentium III processor, the bus speed is generally 133
MHz (although there were a few with 100 MHz). The lowest
bus speed on a Pentium IV is 400 MHz, and there are versions
with much higher speeds (topping at 1066 MHz for the
“extreme edition”).
b. The Pentium 4s are smaller than the Pentium IIIs
c. Pentium III processors had (for the most part. about 512 KB
of cache. Pentium 4 processors, on the other hand, start at 512
KB.
20. What are the differences between Intel Celeron and
Pentium family of Processors?
Celeron
According to Build Gaming Computers, Celeron processors are
the low-end processor intended for standard home computer
use. SciNet reports the best Celeron processor has an L2 Cache
of 128kb, a clock speed limit of about 2.0 GHz and runs at a
core voltage of 1.75V. These are useful numbers for
comparison.
Pentium
The top Pentium processor is the Pentium 4 Prescott. CPU
Scorecard reports it has an L2 cache of 1MB (1024kb), a
potential 3.0 GHz clock speed and runs at about 1.4V. The
lowest performing Pentium 4 processor, the Willamette, has
an L2 cache of 256kb, a potential 2.0 GHz clock speed and
runs at about 1.7V.
21. What is Hyper Threading? What is the use of it?
A thread of execution, or simply a “thread,” is one series of
instructions sent to the CPU. Hyper-threading is a technology
developed to help make better use of spare processing cycles.
Hyper-threaded processors have a duplicate set of registers,
small spaces of high-speed memory storage used to hold the
data that is currently needed to execute a thread. When a CPU
core is delayed, waiting for data to be retrieved from another
place in memory, it can use these duplicate registers to spend
the spare computation cycles executing a different thread. The
second set of registers will be pre-loaded with the data needed
to execute the second thread, so the CPU core can begin work
immediately
22. What is Intel Atom processor?
The Intel Atom family of processors are extremely small
central processing units (CPU. found mostly in ultraportable
devices, such as netbooks, cell phones and tablet PCs,
according to Intel. While small and light on energy use, Atom
processors can handle the most common tasks, such as email
and instant messaging.
23. What is Nehalem Architecture?
Nehalem is Intel’s new microprocessor architecture The Core
i7 chips were the first processors ever produced using an
architecture called Nehalem.
24. Which is a heavy-duty Microprocessor of Intel?
Intel Xeon.
25. Which is the processor suitable from Intel family of
processors for Server and Workstation?
Intel Xeon.
26. What is full name of AMD?
Advanced Micro Devices.
27. What are the latest Processor of Intel and AMD?
For intel it is Intel Core i7 and AMD Opteron 6200 Series
processor.
28. Write socket LGA 775 is apt for which type of Intel
Processors?
The top of the line for the LGA775 series CPU socket was the
Core 2 processor series, with the Core 2 Duo E8600, Core 2
Extreme QX9770 and Core 2 Quad Q9650 being the three top
performers
29. Socket 939 is developed by AMD. It supports a maximum
of how many bits of computing? What are the the different
processors of AMD is suitable for this socket?
AMD Athlon 64, AMD Athlon 64FX and AMD Athlon 64 X2.
30. Which type of socket is needed to connect a dual core
processor of Intel?
Socket LGA 775.
31. What is Heat Sink? What is its use? If it is not in the system
what will happen?
A heat sink is a component used to lower the temperature of a
device.It is most commonly there on the microprocessor. If it
is not properly fixed the system, the system will shutdown
automatically to prevent further damage to the processor.
32. A CPU fan should be placed in system. Why?
To make the system cool and more functioning.
33. What is Upgrading a microprocessor? Why we have to do
it?
34. Upgrading a microprocessor is just physically replacing a
processor with a new one. Before doing so we have to make
sure that the processor we want to use for your upgrade is
physically compatible with the socket on your computer’s
motherboard. We also have to make sure that the motherboard
has the internal logic to support the processor.
35. What are the causes of overheating of microprocessor?
a. Processor fan may not be properly connected.
b. Heat sink may be not contacted with the processor.
c. Jumpers may be configured to over clock the CPU.
d. Voltage supply incompatible
36. No Display. What is the problem?
a. CPU fan problem
b. Heat sink related issue
c. Power related issues
d. Improper Jumper settings
37. What is the use of Conventional memory in the system?
The size of conventional memory is 640KB. It is also called
DOS memory or Base memory. This memory is used by some
small programs like Word star, Lotus etc…DOS cannot use
more than 640KB.
38. What is main memory in a computer?
The main memory in a computer is called Random Access
Memory. It is also known as RAM. This is the part of the
computer that stores operating system software, software
applications and other information for the central processing
unit (CPU. to have fast and direct access when needed to
perform tasks.
39. What is Cache memory? What is the advantage if a
processor with more cache memory you are using?
Cache memory is the memory area between RAM and
Processor. If cache memory increases the speed of the system
will also improved.
40. What are the different types of RAM?
SRAM, DRAM, VRAM, SGRAM, DDR-SDRAM etc….
41. Differentiate SRAM and DRAM.
SRAM
Static RAM stores each bit of data on six metal oxide
semiconductor field effect transistors, or MOSFETs. SRAM is
used in devices that require the fastest possible data access
without requiring a high capacity. Some examples are CPU
caches and buses, hard drive and router buffers and printers.
DRAM
Dynamic RAM stores data using a paired transistor and
capacitor for each bit of data. Capacitors constantly leak
electricity, which requires the memory controller to refresh the
DRAM several times a second to maintain the data.
42. What are the different DRAM types?
FPMDRAM, EDO DRAM, SDRAM, RDRAM, DDR-SDRAM
43. What is the difference between DDR-I and DDR-II?
DDR2 is the successor to DDR RAM. DDR 2 incorporates
several technological upgrades to computer system memory,
as well as an enhanced data rate.DDR 2 is capable of achieving
twice the data transfer rate of DDR-I memory because of its
higher clock speed. It operates at a lower voltage than DDR-I
as well: 1.8 volts instead of 2.5.
44. Which is the latest DDR version? Which processor of Intel
will support it?
The latest DDR version is DDR-III. Intel’s all latest processors
such as Core i3,i5 and i7 will support it.
45. What are VRAM and SGRAM?
VRAM is Video Random Access Memory. Video adapter or
video system uses VRAM. VRAM is dual ported. It is costly.
But SGRAM is not dual ported and not costly. It is a less
expensive approach to graphics functions. Most commonly all
low cost graphics cards are using it.
46. What is SODIMM memory module?
Small outline dual in-line memory module (SODIMM or
SO-DIMM. is a type of random access memory (RAM). It is a
smaller version of a dual in-line memory module (DIMM).It is
the type of the memory module can be used in laptop.
47. Which is the memory packaging suitable for a sub-note
book system?
Micro DIMM
48. What is ECC/EPP?
EPP/ECP (Enhanced Parallel Port/Enhanced Capability Port.
is a standard signaling method for bi-directional parallel
communication between a computer and peripheral devices
that offers the potential for much higher rates of data transfer
than the original parallel signaling methods. EPP is for
non-printer peripherals. ECP is for printers and scanners.
EPP/ECP is part of IEEE Standard 1284.
49. What is over clocking?
Over clocking is the process of forcing a computer component
to run at a higher clock rate.
50. What is memory bank?
Sets of physical memory modules is referred to as memory
banks. A memory bank serves as a repository for data, allowing
data to be easily entered and retrieved.
51. What we need to consider before connecting a memory to
the system?
a. Capacity of the RAM required
b. Check if installed memory is supported by motherboard and
processor
c. Form factor of the RAM
d. Type of RAM needed
e. Warranty of the RAM
52. What is Upgrading the memory?
Adding a memory module to the existing bank on the available
slot or replacing the previous one with the increased memory
size is also called upgrading memory. This will surely increase
the performance of the computer.
53. What is BIOS beep code? What it does mean?
BIOS beep codes are the signs of different issues of the
computer. The beep code may vary depends on the
manufacture of BIOS. For example in case of Award BIOS the
beep code will be,
1 long beep- shows memory problem
1 long beep and 2 short beeps- failure of DRAM parity
1 log beep and 3 short beeps- signifies Video error
Continuous beep- signifies failure in memory or Video
memory.
54. What are Solid State Drive means?
A solid-state drive (SSD), sometimes called a solid-state disk
or electronic disk, is a data storage device that uses solid-state
memory to store data. SSDs use microchips which retain data
in non-volatile memory chips and contain no moving parts.
Compared to electromechanical HDDs, SSDs are typically less
susceptible to physical shock, are silent, have lower access time
and latency, but are more expensive per gigabyte (GB).
55. What is RDRAM?
Short for RAMBUS DRAM, a type of memory (DRAM.
developed by Rambus, Inc.
56. What is SIMM? Is it is using now?
Acronym for Single In line Memory Module, a small circuit
board that can hold a group of memory chips. Typically,
SIMMs hold up to eight (on Macintoshes. or nine (on PCs.
RAM chips. On PCs, the ninth chip is often used for parity
error checking. Unlike memory chips, SIMMs are measured in
bytes rather than bits.
Now a days this memory module is not used.
57. Why do we call motherboard a motherboard?
Motherboard is the basic integrated board of the computer on
which all other components are connected. So that usually we
call motherboard a “motherboard”.
58. What is motherboard? What are the different types of it?
Motherboard is the basic integrated board of the computer on
which all other components are connected. This is classified
mainly into three Desktop, Laptop and Server motherboard.
59. What is the difference between integrated and
non-integrated motherboard?
In integrated motherboard all of the external ports will be
present. But in case of non-integrated motherboard only some
important ports will be available instead of all. The
non-integrated motherboard is an old type of motherboard
which now a day’s not commonly available.
60. How a server motherboard different from a desktop?
A server motherboard is different from a desktop in features
and performance. The number of processor support, RAM
slots ,Expansion card slots etc…are more. For example the
Intel® Server Board S5000PSL has the performance and
features for growing businesses demand. It provides excellent
data protection, and advanced data management. It support
64-bit Multi-Core Intel® Xeon® processor. Eight fully
buffered 533/667 MHz DIMMs. Up to six SATA 3Gb/s ports.
61. What is form factor of motherboard?
The form factor of a motherboard determines the
specifications for its general shape and size. It also specifies
what type of case and power supply will be supported, the
placement of mounting holes, and the physical layout and
organization of the board. Form factor is especially important
if you build your own computer systems and need to ensure
that you purchase the correct case and components.
62. What is ATX? How it is different from AT? Which is using
now?
AT is a short for advanced technology, the AT is an IBM PC
model introduced in 1984. It includes an Intel 80286
microprocessor, a 1.2MB floppy drive, and an 84-key AT
keyboard. The ATX form factor specified changes to the
motherboard, along with the case and power supply. Some of
the design specification improvements of the ATX form factor
included a single 20-pin connector for the power supply, a
power supply to blow air into the case instead of out for better
air flow, less overlap between the motherboard and drive bays,
and integrated I/O Port connectors soldered directly onto the
motherboard. The ATX form factor was an overall better
design for upgrading.
63. What is the need of expansion slot in motherboard?
Alternatively referred to as an expansion port, an expansion
slot is a slot located inside a computer on the motherboard or
riser board that allows additional boards to be connected to it.
64. What is PCI slot? How is different from PCI Express
(PCI-E)?
Short for PERIPHERAL COMPONENT INTERCONNECT, a
local bus standard developed by Intel Corporation. PCI
Express (Peripheral Component Interconnect Express),
officially abbreviated as PCIe, is a computer expansion card
standard designed to replace the older PCI, PCI-X, and AGP
bus standards.
65. What is AGP slot? What is its use?
The Accelerated Graphics Port (often shortened to AGP. is a
high-speed point-to-point channel for attaching a video card to
a computer’s motherboard, primarily to assist in the
acceleration of 3D computer graphics. Since 2004 AGP has
been progressively phased out in favor of PCI Express (PCIe).
66. What is jumper? What is the need?
A metal bridge that closes an electrical circuit. Typically, a
jumper consists of a plastic plug that fits over a pair of
protruding pins. Jumpers are sometimes used to configure
expansion boards. By placing a jumper plug over a different set
of pins, you can change a board’s parameters.
67. What CMOS and CMOS battery?
Short for complementary metal oxide semiconductor.
Pronounced see-moss. The CMOS chip holds the date, time,
and system setup parameters. This chip is powered by a 3Volt
CMOS battery.
68. What is chipset?
A number of integrated circuits designed to perform one or
more related functions. This is one of the processing device in
a computer.
69. Explain any three Intel chipset?
a. Intel P55 Express Chipset.-Desktop PC platforms based on
the Intel® P55 Express Chipset combined with the Intel®
Core™ i7-800 series processors and Intel® Core™ i5-700
series processors create intelligent performance for faster
multi-tasking, digital media creation and gaming.
b. Intel HD55 Express Chipset- a new architecture designed to
deliver quality, performance, and industry-leading I/O
technologies on platforms powered by the Intel® Core™
i7-800, Intel® Core™ i5, and Intel® Core™ i3 processors.
c. Intel E7500 Chipset- a volume chipset supports
dual-processor (DP. server systems optimized for the Intel®
Xeon® processor.
70. Which is the chipset needed for Intel Core i7 and Core i5
processors?
Intel Core i7 900-series uses x58 chip set and Core i7
800-series and Core i5 processors runs on P55 chipset.
71. Which is the socket used by Intel Core i7 and i5 processors?
Intel Core i7 900-series uses LGA1366 socket and Core i5
CPUs–all three run on Intel’s latest P55 chipset and LGA1156
socket.
72. What are the motherboard manufacturing companies?
Intel, Gigabyte, ASUS, Mercury, HP, Acer, Biostar, Compaq,
Digital, IBM, AMI.
73. Before upgrading/replacing a motherboard what you need
to consider?
a. Power Connectors
b. Memory Support
c. Hard Disk Support
d. System Case
74. Can you upgrade motherboard?
Yes
75. One system is not starting, but the fan is working. What is
the problem?
76. What is Intel LGA 1155 Socket?
LGA 1155, also called Socket H2, is an Intel microprocessor
compatible socket which supports Intel Sandy Bridge and the
up-coming Ivy Bridge microprocessors.LGA 1155 is designed
as a replacement for the LGA 1156 (known as Socket H).
77. What is power supply unit?
A power supply unit (PSU. supplies direct current (DC. power
to the other components in a computer. It converts generalpurpose
alternating current (AC. electric power from the
mains to low-voltage (for a desktop computer: 12 V, 5 V, 5VSB,
3V3, -5 V, and -12 V. DC power for the internal components of
the computer.
78. What are the different types of Form Factors of Power
Supply?
AT , ATX, Flex ATX, Micro ATX etc…
79. What is NLX?
NLX (New Low Profile Extended. was a form factor proposed
by Intel and developed jointly with IBM, DEC.
80. What is Switching Mode Power Supply?
A switched-mode power supply (switching-mode power
supply, SMPS, or simply switcher. is an electronic power
supply that incorporates a switching regulator in order to be
highly efficient in the conversion of electrical power. Like other
types of power supplies, an SMPS transfer power from a
source like the electrical power grid to a load (e.g., a personal
computer. while converting voltage and current
characteristics. An SMPS is usually employed to efficiently
provide a regulated output voltage, typically at a level different
from the input voltage.
81. What is the use of Molex Power connector?
Molex is a four pin power connector found in SMPS. It is used
to supply power to HDD, CD Drive, DVD Drive etc…
82. What is Berg (mini Molex. connector is used to….
To provide power to Floppy Disk Drive.
83. What are the different color cables found in Molex
connector? What is the Power of it.
-12V –Blue, -5V –White, 0V –Black, +3.3V –Orange, +5V
–Red, +12V –Yellow.
84. What are the methods used in a system for cooling?
a. Large System Case
b. Arrangement of Internal Components
c. Keeping the System Clean.
d. Proper Working of the System Case Fan.
85. Power supply fan is not working and it emits a lot of sound.
What will the probable cause?
Most of the time this issue arises due to lots of dust is
accumulated on the fan motor.
86. What is the capacity of a Floppy Disk?
1.44MB
87. Which is the medium used in a floppy for storing data?
Magnetic Media.
88. What is write protected notch in a floppy? What is its use?
This is a switch used to eliminate the accidental deletion of
data from the floppy.
89. How many tracts and sectors found in a normal floppy
dick?
80 tracks and 18 sectors.
90. Which is the file system of a floppy disk?
FAT
91. How can you format a floppy? What is happening if you do
so?
Insert the floppy to the system and open my computer. There
we can find the icon. Just right click and select format option.
Otherwise we can use format command . Formatting a floppy
will creates sectors and tracks on the floppy.
92. System is not showing floppy disk drive icon in
Mycomputer.What will the probable cause?
The device is not detected or disabled.
93. I have inserted a new floppy disk into my drive. The data
can be read. But not able to make modifications. Why?
The disk may be in write protected mode.
94. What is HDD? What are the different types available in the
market now?
A hard disk drive (HDD; also hard drive or hard disk. is a
non-volatile, random access digital magnetic data storage
device. It is the secondary storage media. There are different
types of hard disk, based on the the intefaces they used we can
classify them as IDE, SATA, SCSI etc…
95. What is SATA?
Serial ATA (SATA or Serial Advanced Technology Attachment.
is a computer bus interface for connecting host bus adapters to
mass storage devices such as hard disk drives and optical
drives. Serial ATA was designed to replace the older parallel
ATA (PATA. standard (often called by the old name IDE),
offering several advantages over the older interface: reduced
cable size and cost (7 conductors instead of 40), native hot
swapping, faster data transfer through higher signalling rates,
and more efficient transfer through an (optional. I/O queuing
protocol.
96. In Speed how SATA is different from IDE?
SATA- Serial Advanced Technology Attachment (SATA. is high
speed serial interface designed to replace IDE and EIDE drive
standard SATA has a seven pin connector. SATA transfer
speed of data up to 600 MB per second. Now a day use SATA.
IDE- Integrated Drive Electronics (IDE. it has a 40/80 pins
connector. IDE transfer speed of data up to 100/133 MB per
second few time ago mostly use IDE.
97. What is eSATA?
External Serial Advanced Technology Attachment or eSATA is
an external interface for SATA technologies. eSATA cables are
narrow and can be up to 6.56 feet (2 meters. in length. eSATA
requires its own power connector. It is still an excellent choice
for external disk storage.
98. What is SCSI? Is the SCSI Hard Disk is needed for a home
purpose?
SCSI is Small Computer System Interface , is a type of
interface used for computer components such as hard drives,
optical drives, scanners and tape drives. SCSI is a faster, more
robust technology than IDE amd SATA, and has traditionally
been utilized in servers. Aside from speed, another great
advantage over IDE and SATA is that the SCSI card can
connect 15 or more devices in a daisy chain. The controller
assigns each device its own SCSI ID, allowing for great
flexibility towards expanding any system. It is more costly. It is
not needed for a home purpose.
99. Is there is USB HDD? If yes what is the speed?
Yes. If your HDD is based on USB 3.0 it can offer a maximum
transmission speed of up to 5 Gbit/s (640 MB/s), which is over
10 times faster than USB 2.0 (480 Mbit/s, or 60 MB/s).
100. What is IEEE 1394 Interface?
The IEEE 1394 interface is a serial bus interface standard for
high-speed communications. The interface is also known by
the brand names of FireWire (Apple), i.LINK (Sony), and Lynx
(Texas Instruments). IEEE 1394 replaced parallel SCSI in
many applications, because of lower implementation costs and
a simplified, more adaptable cabling system. The original
release of IEEE 1394-1995 specified what is now known as
FireWire 400. It can transfer data between devices at 100,
200, or 400 Mbit/s.
Original link to the article is here:
All posts
What are Malware and Computer Viruses?
Computer Physicians, LLC Colorado customers frequently ask many questions about their computers. Therefore we have created a blog to help customers understand some topics in the computer and internet world.
What is Malware?
Malware is short for “malicious software.” Malware is any kind of unwanted software that is installed without your adequate consent. Viruses, worms, and Trojan horses are examples of malicious software that are often grouped together and referred to as malware.
These Are A Few Of The Signs That Malware Has Entered Your PC:
- You start seeing an excessive amount of pop-up ads.
- Your PC’s operating system slows down significantly.
- The amount of spam you receive in your email increases.
- Your email account may send out messages to your contact list that you did not send. Sometimes it contains pornographic material or even a trojan or worm.
- The home page you have set in your browser is altered.
- When you try to access a web page in your favorites list, another web page appears that contains advertising or content that encourages you to enter your personal information.
- Your computer completely crashes.
- You are unable to access your antivirus program to remove the malware.
If your computer has become unstable, that’s a sign that something’s wrong. Some malware messes with important files that keep your computer running properly. That could cause your computer to crash. If your computer crashes when you try to run a specific application or open a particular file that tells you that something has corrupted the data. It could be malware.
Does your computer seem to run much more slowly than it used to? This could be the result of malware as the malicious code begins to drain your computer’s processing resources. If you aren’t running a resource-heavy application but your computer is very slow, you might have a computer virus.
Strange messages indicating that you can’t access certain drives on your computer are another sign that something is wrong. In a similar vein, applications that won’t run or files that won’t open may also be the result of infection. Other indicators include hardware (like printers) that no longer responds to commands. While none of these guarantee the presence of a virus, they do suggest that something is wrong with your machine.
If you notice that file sizes are fluctuating even if you aren’t accessing those files, that’s another sign of a computer virus. And finally, if you access menus and their appearance is odd or distorted, you could be the victim of a malware attack.
It’s important to remember that computer viruses are one potential cause of problems like the ones we’ve listed here, but that they aren’t the only cause.
Types of Malware
The more you educate yourself on malicious software, the better off you’ll be. Malware is not a virus. In fact, it consists of viruses, worms, Trojan horses, adware, rootkits and many other nasty infections. Some of these programs are more of an annoyance than anything, while others pose a serious threat to your computer. Regardless of the type, each of them offer their own unique security threat, and they should be avoided at all costs.
Viruses
The computer virus is the most infamous form of malware. It is a self replicating program that infects a system without authorization. A virus is often transmitted via email but can also be distributed through various storage mediums such as a flash drive. Once installed, it will execute itself, infect system files, and attempt to propagate to other systems. The impact of a virus ranges widely from slow system performance to wiping out every file on your computer.
Worms
Though closely related, worms and viruses are two completely different types of malware. Both have the ability to self-replicate and propagate by attaching themselves to files. While a virus moves from machine to machine with the help of a human, a worm tends to leach onto network traffic and can be a corporation’s worst nightmare. In no time, it can travel through the internet and inflict great damage from deleting files to creating backdoors that give its creator control of a system.
Trojan Horses
Similar to the mythical wooden horse used by the Greeks to invade Troy, the Trojan horse is a very deceptive program that appears harmless but is actually one of the most dangerous types of malware. It may arrive as a friendly email attachment or present itself as a useful application on a website. Because it does not have the ability to self replicate, a Trojan cannot be classified as a virus. However, it does have the ability to deliver destructive payloads and unload viruses, worms or spyware.
Spyware
Spyware is a sneaky program that tracks and reports your computing activity without consent. While it isn’t designed to inflict damage, spyware can terribly affect the performance of your computer over time. Spyware usually comes bundled with free software and automatically installs itself with the program you intended to use. Signs of spyware include sudden modifications to your web browser, redirects of your search attempts and the frequent displaying of pop-ups. In this instance, spyware can also be termed as adware which is essentially add-supported software that has the ability to track your activity.
Rootkits
A rookit could be a single program or collection of programs designed to take complete control of a system. This type of malware is employed by hackers and gives them all the abilities of a system administrator from a remote location.
Rootkits are very sophisticated as they make hackers very difficult to find. They are often used to infect other computers and enslave them as zombies, forcing them to attack other machines, distribute spam or steal passwords. When attempting to track a rootkit’s creator, the search usually ends with the first zombie while the hacker goes undetected.
Staying Safe
As you can see, malware is abundant and will attempt to attack your from every direction. However, there are several security solutions and system updates that will help to keep you protected. Combine these tools with safe computing and you have a much better chance of keeping the malicious software away.
_______________________________________________________________
Computer Physicians, LLC Colorado provides:
- System Crash Recovery
- Data Recovery
- Internet setup
- Computer, internet, and network Troubleshooting
- Virus, spyware, malware, and adware removal
- Hardware and software computer repair
- Computer Sales, systems, parts
- Upgrades and Installations
- Building PC computer systems
- tutoring & training
- Computer and network security
- Computer PC repair
Located in Erie, CO we service the Colorado front range, including:
Erie, Boulder, Longmont, Denver, Brighton, Louisville, Lafayette, Fredrick, Firestone, Fort Lupton, Thornton, Northglenn, Arvada, Superior, Broomfield, Gunbarrel, Henderson, Englewood, Aurora, Lakewood, Berthoud, Lyons, Niwot, Dacono, University of Colorado at Boulder, Weld and Boulder counties, and surrounding areas of Colorado.