Computer Physicians, LLC Colorado customers frequently ask many questions about their computers. Therefore we have created a blog to help customers understand some topics in the computer and internet world.
What is the internet?
The Internet Is a Big Network of Computers.
The Internet is named for “interconnection of computer networks”. It is a massive hardware combination of millions of personal, business, and governmental computers, all connected like roads and highways. The Internet started in the 1960’s under the original name “ARPAnet”. ARPAnet was originally an experiment in how the US military could maintain communications in case of a possible nuclear strike. With time, ARPAnet became a civilian experiment, connecting university mainframe computers for academic purposes. As personal computers became more mainstream in the 1980’s and 1990’s, the Internet grew exponentially as more users plugged their computers into the massive network. Today, the Internet has grown into a public network of millions of personal, government, and commercial computers, all connected by cables and by wireless signals.
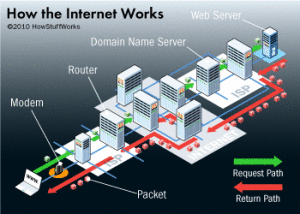
No single person owns the Internet. No single government has authority over its operations. Some technical rules and hardware/software standards enforce how people plug into the Internet, but for the most part, the Internet is a free and open broadcast medium of hardware networking.
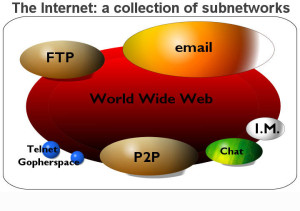
2: The Web Is a Big Collection of HTML Pages Within the Internet.
The World Wide Web, or “Web” for short, is the very large subset of the Internet dedicated to broadcasting HTML pages. The Web is viewed by using free software called web browsers. Born in 1989, the Web is based on hypertext transfer protocol, the language which allows you and me to “jump” (hyperlink) to any other public web page. There are over 90 billion public web pages on the Web today, and over 300 billion private (‘invisible’) web pages.
_______________________________________________________________
Computer Physicians, LLC Colorado provides:
- System Crash Recovery
- Data Recovery
- Internet setup
- Computer, internet, and network Troubleshooting
- Virus, spyware, malware, and adware removal
- Hardware and software computer repair
- Computer Sales, systems, parts
- Upgrades and Installations
- Building PC computer systems
- tutoring & training
- Computer and network security
- Computer PC repair
Located in Erie, CO we service the Colorado front range, including:
Erie, Boulder, Longmont, Denver, Brighton, Louisville, Lafayette, Fredrick, Firestone, Fort Lupton, Thornton, Northglenn, Arvada, Superior, Broomfield, Gunbarrel, Henderson, Englewood, Aurora, Lakewood, Berthoud, Lyons, Niwot, Dacono, University of Colorado at Boulder, Weld and Boulder counties, and surrounding areas of Colorado.
Like this:
Like Loading...